The Cyber Kill Chain offers a comprehensive framework as a part of the Intelligence Driven Defense model. In this article, we will discuss what the cyber kill chain is and what its steps are. Cyber intrusions are the worst nightmare of many of us. That is why many cyber security professionals and developers offer unique solutions for the identification and prevention of cyber intrusions activity. Being one of those developers, Lockheed Martin has brought the Cyber Kill Chain into our lives. In this article, we will explain what Cyber Kill Chain is in great detail and also provide a comprehensive, 7-step guide. Keep reading to learn!
What is the Cyber Kill Chain?
The term kill chain was first used as a military concept that defines the structure of an attack that covers:
- The identification of the target
- The force dispatch towards the target
- The decision and order to attack the target
- The destruction of the target
The idea of interrupting the opponent’s kill chain activity is often employed as a defense. Inspired by the whole kill chain concept, Lockheed Martin (an aerospace, security, arms, defense and advanced technologies company based in the United States of America) created the Cyber Kill Chain. It is a
cybersecurity framework that offers a method to deal with the intrusions on a computer network.
Since it first emerged, the Cyber Kill Chain has evolved significantly in order to anticipate and recognize insider threats much better, detect various other attack techniques like advanced ransomware and social engineering.
The Cyber Kill Chain consists of seven steps that aim to offer a better attack visibility while supporting the cyberattack / cybersecurity analyst to get a better understanding of the adversary’s tactics, procedures and techniques. The seven steps of the Cyber Kill Chain illustrates the different phases of a cyberattack starting from reconnaissance, reaching to the exfiltration.
What are the 7 steps of the Cyber Kill Chain?
The Cyber Kill Chain consists of 7 steps: Reconnaissance, weaponization, delivery, exploitation, installation, command and control, and finally, actions on objectives. Below you can find detailed information on each.
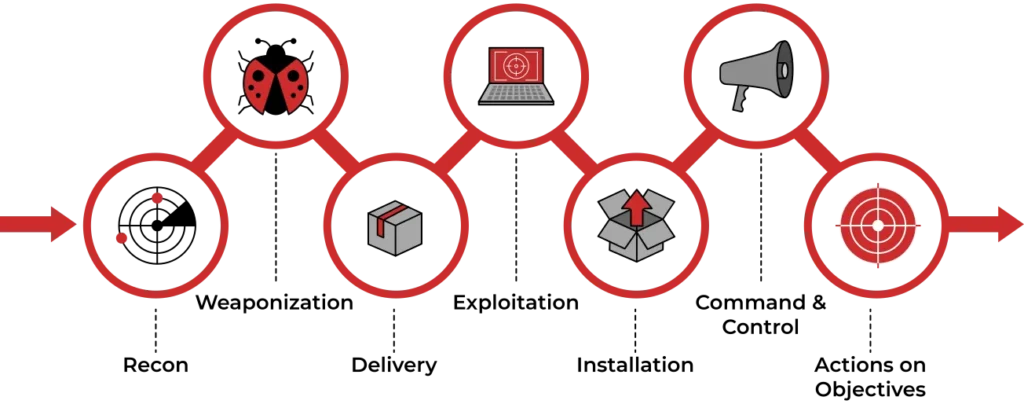
- Reconnaissance: In this step, the attacker / intruder chooses their target. Then they conduct an in-depth research on this target to identify its vulnerabilities that can be exploited.
- Weaponization: In this step, the intruder creates a malware weapon like a virus, worm or such in order to exploit the vulnerabilities of the target. Depending on the target and the purpose of the attacker, this malware can exploit new, undetected vulnerabilities (also known as the zero-day exploits) or it can focus on a combination of different vulnerabilities.
- Delivery: This step involves transmitting the weapon to the target. The intruder / attacker can employ different methods like USB drives, e-mail attachments and websites for this purpose.
- Exploitation: In this step, the malware starts the action. The program code of the malware is triggered to exploit the target’s vulnerability/vulnerabilities.
- Installation: In this step, the malware installs an access point for the intruder / attacker. This access point is also known as the backdoor.
- Command and Control: The malware gives the intruder / attacker access in the network/system.
- Actions on Objective: Once the attacker / intruder gains persistent access, they finally take action to fulfil their purpose, such as encryption for ransom, data exfiltration or even data destruction.



