Upgrading software is continuous and non ending process for networking devices to secure your network infrastructure. Specially when we are facing continuous cyber attack over network infrastructure, upgrading software to latest available version helps to prevent loosing data. Upgrade can be Major, Minor or Hotfix for specific bug and and each upgrade adds more security to your infrastructure.
In this post we will discuss about upgrading procedure for Paloalto networks. Paloalto software is called PANOS and currently PAN OS 10 is latest one. We will see how to upgrade Paloalto device in High Availability (HA) cluster.
Software version can be listed like 10.1.2 where 10 is Major release, 1 is minor release, 2 is patch and also can be listed like 10.1.2-h2, where h2 is hotfix for specific bug/issue.
To avoid downtime when upgrading firewalls that are in a high availability (HA) configuration, update one HA peer at a time: For active/active firewalls, it doesn’t matter which peer you upgrade first (though for simplicity, this procedure shows you how to upgrade the active-primary peer first). For active/passive firewalls, you must suspend (fail over) and upgrade the active (primary) peer first. After you upgrade the primary peer, you must unsuspend the primary peer to return it to a functional state (passive). Next, you must suspend the passive (secondary) peer to make the primary peer active again. After the primary peer is active and the secondary peer is suspended, you can continue the upgrade. To prevent failover during the upgrade of the HA peers, you must make sure preemption is disabled before proceeding with the upgrade. You only need to disable preemption on one peer in the pair. Let’s see below in detail:
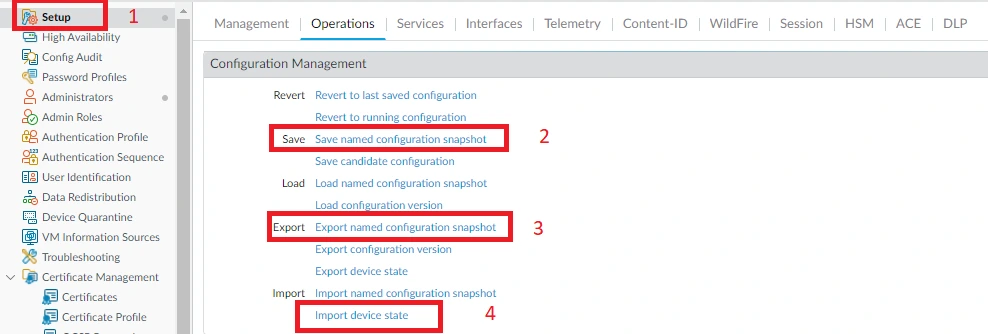
Step 1: Save a backup of the current configuration file.
- Go to device > Setup > Operations and click Save name configuration snapshot (Give custom name to file)
- Go to device > Setup > Operations and click Export named configuration snapshot (select name given above and click ok)
- Additionally, Export Device state file. Click Import device state
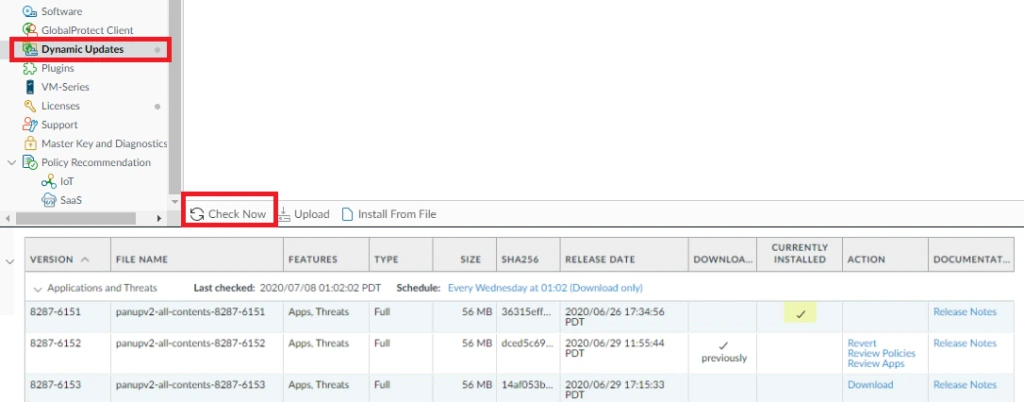
Step 2: Ensure that each firewall in the HA pair is running the latest content release version.
- Go to Device > Dynamic update and check Application or Application and Threats.
- If latest update available click on Downlead and after download Install the update. You must install the update on both peers.
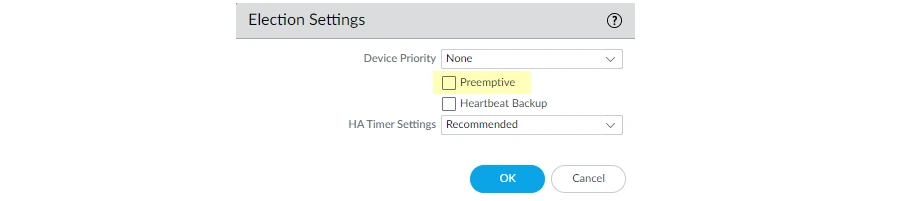
Step 3: Disable preemption on the first peer in each pair. You only need to disable this setting on one firewall in the HA pair but ensure that the commit is successful before you proceed with the upgrade.
- Go to Device > High Availability and edit election setting.
- Uncheck Preemptive box if checked.
- Commit the change.
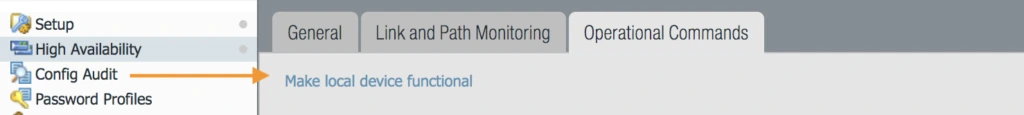
Step 4: As a best practice before upgrading you can failover the device and verify traffic so that you won’t face any issue after upgrade.
- To failover go to Device > High Availability > Operation Commands and Suspend local device on Active Firewall (Once you click Suspend local device, make local device functional option will be available at same place.). Once you do this Active will become non-functional and Passive will become Active.
- Once Passive becomes Active, make current device functional, this will make this device Passive.
Step 5: Now start upgrading passive device first. only perform 1 step upgrade at a time.
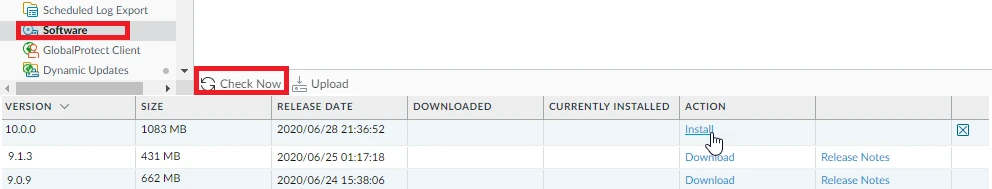
- Go to Device > Software > click on Check now at bottom.
- Download desire version, once completed Install it. Once Installation is done, PA will ask to Reboot device, click ok and wait for 10-15 minutes based on device model and configuration data size.
- You can perform continuous ping on firewall to know when it’s up.
- Once device is up and GUI is available you need to wait 2 more minutes to login, otherwise it will display incorrect username/password.
Step 6: Once device is up, login and verify configuration. You ca check policy available, Objects, network interfaces etc. As a best practice you can take fresh backup after upgrade.
Step 7: Now your can perform failback to newly upgraded Paloalto firewall. Repeat Step 4, this will make upgraded device active and non upgraded passive. You can verify Traffic and Services from Upgraded device before moving to second device upgrade process.
Step 8: Once you verify traffic/services from upgraded device you can move to upgrade current passive (second device). You can follow Step 5 and Step 6.
Step 9: Once both device are upgraded you can verify from dashboard and you can enable Preemption if it was.
Key point to note:
- Perform 1 step upgrade at a time.
- If you are upgrading from 8.1.0 to 9.1.0 the path will be 8.1.0 -> 8.1.23 (latest available upgrade), 8.1.23 -> 9.0.0 download & 9.0.16-h2 (only download base version and install latest available upgrade), 9.0.16-h2 -> 9.1.0 download & install. ( If you wan to install 9.1.13, download 9.1.0 and download & install 9.1.13)
- If your firewalls are managed by panorama, Panorama PANOS version should be same or higher then firewall.
- After every Installation reboot device, do failover and test traffic, upgrade both active and passive one by one and take backup.







